Secrets Management
The Secrets page provides an interface for managing sensitive credentials used by Super.Human.Installer (SHI), primarily for accessing private Git repositories.
Overview
Sensitive information like API keys should not be hardcoded. The Secrets page allows you to securely store and manage credentials needed for specific SHI features, such as importing provisioners from private GitHub repositories.
Access this page via Settings -> Manage Global Secrets.
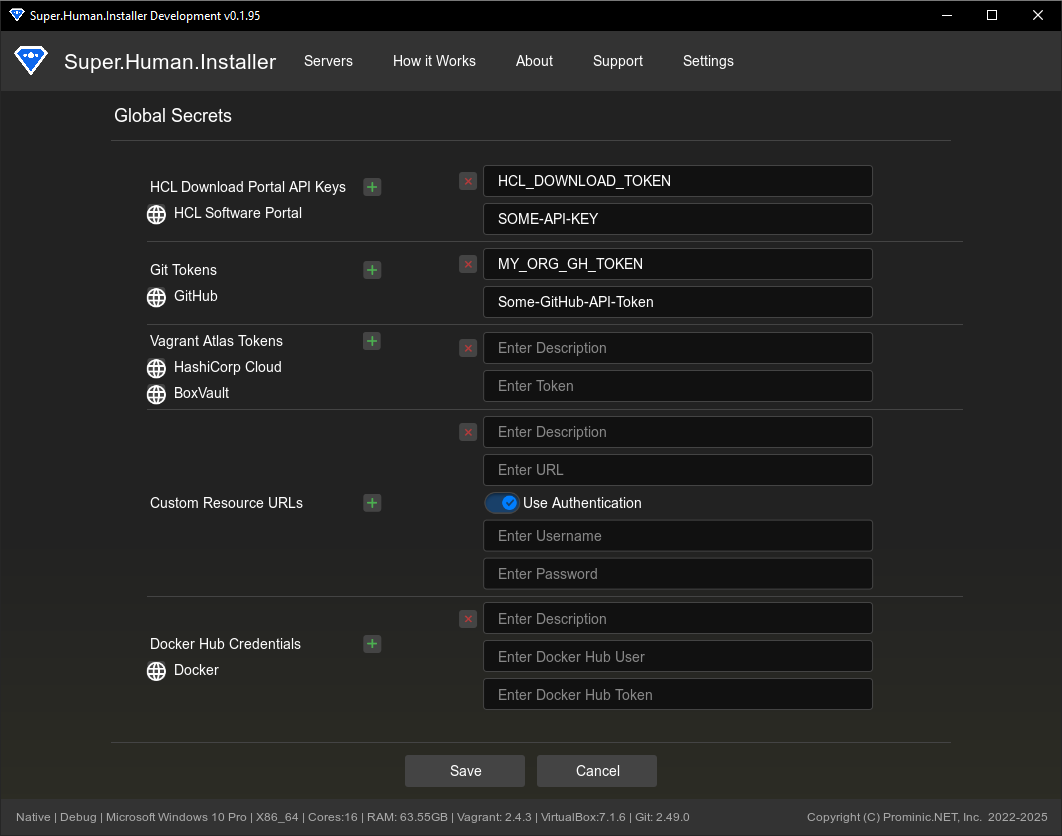
HCL Download Portal API
You can add a HCL API key, which will allow you to download the various Binaries from HCL Downloads to use without having to manually find/download and locate the various installer binaries/archives.
You can add multiple keys should you have multiple accounts.
Note: HCL API keys are one time use! If you use the Key before you add it to SHI it will fail. The HCL API Key, is actually a Refresh token, which when first used, exchanges with the HCL servers an “Access Token”, This access token is periodically refreshed. SHI does not expose this Access Token as it is not meant for re-use.
To add a API key, Select the Green + Icon on the Manage Global Secrets Page. This will prompt you for two fields.
Then login to the HCL Downloads portal, once you have logged in, in the upper right hand of the page, you should see your Profile. Select your profile, and in the drop down select Manage API Keys.
In the Manage API Keys page, create a new API, It is best practice to name the API and use the same name in the description field in SHI.
Copy the API key to SHI in the API Key Field. Then click Save.
Once this has been completed you can download various software packages via the File Cache
Git API Keys / Personal Access Tokens (PATs)
Git API keys (often called Personal Access Tokens or PATs on platforms like GitHub, GitLab, Bitbucket) allow SHI to authenticate with private Git repositories when using the “Import from GitHub” feature on the Provisioner Import page.
Managing Git API Keys
- Adding a Key:
- Click “Add”.
- Enter a descriptive Name for the token (e.g., “My GitHub PAT”).
- Paste the actual API Key / Token value obtained from your Git provider (e.g., GitHub Developer Settings).
- Click “Save” in the row.
- Editing a Key:
- Click “Edit” next to an existing key.
- Modify the Name or Key value.
- Click “Save” in the row.
- Deleting a Key:
- Click “Delete” next to the key you want to remove.
Changes are saved only when you click the main “Save” button at the bottom of the Secrets page.
Usage
When using the “Import from GitHub” feature on the Provisioner Import page, the “GitHub Token” dropdown will be populated with the names of the keys you’ve saved here. Selecting a token allows SHI to clone private repositories associated with that token. Choose “None” for public repositories.
SSH Keys
You can Add SSH keys and reference them in a Hosts.template.yml by using the SSH Keys description in between the :: delimeters.
Security Considerations
- Secrets are stored within the main SHI configuration file (
.shi-config) in your user’s application storage directory. Ensure this file is adequately protected according to your system’s security practices. - Use tokens/keys with the minimum required permissions (e.g., read-only access to specific repositories).
- Use tokens with expiration dates where possible.
- Regularly review and rotate your keys/tokens according to security best practices.
Relevant Files
- Source/superhuman/components/SecretsPage.hx - UI implementation for this page.
- Source/superhuman/config/SuperHumanSecrets.hx - Data structure definition for secrets.
- Source/superhuman/config/SuperHumanConfig.hx - Main configuration where secrets are stored.
- Source/superhuman/managers/ProvisionerManager.hx - Uses saved Git tokens during GitHub imports.